Data privacy laws 2025 present a fascinating and complex landscape, poised to significantly reshape how businesses and individuals interact with data. Anticipated changes to data subject rights, security protocols, and cross-border transfer mechanisms will impact industries worldwide. This guide delves into the key elements of these evolving regulations, providing a comprehensive overview and addressing potential implications for all stakeholders.
The year 2025 promises a new era in data governance. This shift necessitates a deep understanding of emerging regulations and their impact on various sectors. The forthcoming laws will address data security, subject rights, and international cooperation. Navigating this evolving landscape requires careful consideration of potential challenges and opportunities.
Overview of Data Privacy Laws
Anticipated data privacy laws for 2025 are poised to significantly reshape how organizations handle personal data. These laws will likely introduce stricter regulations, impacting various sectors and requiring substantial adjustments in data management practices. Understanding these emerging regulations is crucial for businesses seeking to navigate the evolving landscape and maintain compliance.
Anticipated Data Privacy Laws in 2025
The projected data privacy laws for 2025 will likely emphasize comprehensive data protection, focusing on user consent, data minimization, and security measures. These regulations are expected to incorporate principles of transparency and accountability, holding organizations responsible for how they collect, use, and share personal data. This proactive approach aims to address the increasing risks associated with data breaches and misuse.
Potential Impact on Industries
The anticipated data privacy laws will have a broad impact across various sectors. Financial institutions, for instance, will face heightened scrutiny regarding the security and handling of sensitive financial information. E-commerce companies will need to meticulously document user consent and provide clear privacy policies, impacting customer experience and marketing strategies. Healthcare organizations will be subject to stringent rules regarding patient data protection, potentially impacting research and treatment accessibility.
These laws will also affect social media platforms and other online services.
Key Principles of Emerging Regulations
The core principles underpinning these regulations are user empowerment, data minimization, and robust security measures. Users will have greater control over their data, with clearer rights to access, rectify, and delete information. Data will be collected only as necessary, minimizing potential risks of misuse. Organizations will be required to implement strong security protocols to safeguard user data from unauthorized access and breaches.
Examples of these principles include the right to be forgotten, data portability, and limitations on data retention periods.
Comparison of Current and Projected Laws
| Feature | Current Laws (e.g., GDPR, CCPA) | Projected Laws (2025) ||—|—|—|| Scope | Primarily focused on EU/California | Potentially global or regional expansion || Data Breach Notification | Mandated but with varying thresholds | Increased frequency and detail required || Data Subject Rights | Increasing emphasis on rights like access and rectification | Enhanced rights, potentially including right to data erasure and data portability || Cross-Border Data Transfer | Complex regulations and mechanisms | Potentially harmonized rules and streamlined mechanisms || Enforcement Mechanisms | Penalties and fines | Increased financial penalties and potentially broader legal repercussions |
Examples of Potential Differences
Current data privacy regulations may not encompass all data categories, including sensitive biometric data or personal data from emerging technologies like AI. Projected laws might introduce stricter requirements for handling such data. Furthermore, the focus on user consent and control over data may be even more pronounced, demanding detailed consent mechanisms and easily accessible user interfaces for data management.
Existing laws may lack provisions for certain emerging technological challenges, requiring future regulations to incorporate these aspects. The increased use of AI and machine learning is expected to lead to new data privacy considerations in 2025, demanding more precise and adaptable regulations.
Data Subject Rights and Responsibilities
Data privacy laws are evolving, and 2025 will likely see significant changes in data subject rights. These rights, alongside the corresponding responsibilities of organizations, are crucial for ensuring individuals have control over their personal information. The increasing digitization of our lives necessitates robust frameworks for data protection.Data subjects are now empowered with a broader array of rights regarding their personal information.
Organizations are obligated to respect these rights and ensure compliance. Understanding these rights and responsibilities is essential for both individuals and businesses in the digital age.
Anticipated Changes to Data Subject Rights in 2025
Existing data privacy laws, such as GDPR and CCPA, have established a foundation for data subject rights. However, 2025 is expected to bring further refinements and expansions to these rights. For instance, we can anticipate the recognition of a right to data portability across more sectors and an enhanced right to erasure (the “right to be forgotten”). Furthermore, there might be new provisions related to the use of AI and automated decision-making processes involving personal data.
These developments aim to better protect individuals from misuse and abuse of their information.
Key Responsibilities of Organizations
Organizations collecting and processing personal data bear significant responsibilities under evolving privacy laws. These responsibilities include implementing appropriate technical and organizational measures to safeguard data, providing clear and concise information about data collection practices, and facilitating data subject access and correction requests. Transparency and accountability are paramount. Organizations need to demonstrate due diligence in their data handling practices.
This includes demonstrating compliance with the regulations and responding promptly to data subject requests.
Data Subject Rights Granted
This section Artikels the fundamental rights granted to data subjects under anticipated 2025 legislation.
- Right to Access: Individuals have the right to request and obtain information about how their data is being collected, used, and shared. This includes details on the purpose of data collection, categories of data processed, and recipients of the data.
- Right to Rectification: Data subjects can request corrections or updates to inaccurate or incomplete data held by organizations. This ensures data accuracy and prevents potential harm.
- Right to Erasure (“Right to be Forgotten”): Under specific conditions, individuals may request the deletion of their personal data. This right aims to limit the retention of personal data beyond what is necessary.
- Right to Restriction of Processing: Data subjects can request that the processing of their data be limited, for instance, during a dispute about the accuracy of the data. This allows individuals to pause data use while a dispute is being resolved.
- Right to Data Portability: Data subjects have the right to receive their personal data in a structured, commonly used, and machine-readable format. This enables easier transfer of data between different services.
- Right to Object: Data subjects have the right to object to certain data processing activities, particularly in cases of direct marketing or profiling.
- Right to Withdraw Consent: Individuals can revoke their consent for data processing at any time. This is particularly important for data collected based on consent.
Comparison of Data Subject Rights Across Jurisdictions
Data subject rights vary across different jurisdictions. For example, the GDPR in Europe is known for its comprehensive approach, while the CCPA in California focuses on consumer data. Comparing the rights across jurisdictions highlights the diversity of approaches and the need for international harmonization.
| Jurisdiction | Key Data Subject Rights | Specific Provisions |
|---|---|---|
| European Union (GDPR) | Access, rectification, erasure, restriction of processing, data portability, object, and withdrawal of consent. | Emphasis on strong individual rights and high standards of data protection. |
| California (CCPA) | Access, deletion, and data portability. | Focuses on consumer rights regarding personal information collected by businesses. |
| Other Jurisdictions | Varying rights and specific provisions | Each jurisdiction has unique considerations and specific legal frameworks. |
Structuring Information about Data Subject Rights in a User-Friendly Format
Providing clear and accessible information about data subject rights is crucial. Organizations should use plain language, avoiding complex legal jargon. Visual aids, such as flowcharts or FAQs, can enhance understanding. This user-friendly approach is vital to ensure individuals can effectively exercise their rights.
International Harmonization and Cooperation: Data Privacy Laws 2025
International data privacy is increasingly complex, requiring a global approach to address the challenges of cross-border data flows. Countries are recognizing the need for greater cooperation and harmonization of their data privacy laws to ensure consistency and prevent fragmentation. This necessitates a collaborative effort to establish common standards that can effectively address the multifaceted nature of data privacy concerns in the digital age.The current landscape of data privacy regulations exhibits considerable variation across jurisdictions.
This diversity, while reflecting differing cultural and societal contexts, often leads to complexities in managing data that traverses international boundaries. Effective data governance requires a shared understanding of fundamental principles and a coordinated framework to manage the intricate interplay of international data flows.
Efforts Towards International Harmonization
Efforts towards international harmonization of data privacy laws are underway, primarily through the work of international organizations and collaborative initiatives between countries. These efforts aim to develop common principles and guidelines that can be incorporated into national legislation, facilitating cross-border data transfers. Key international organizations, such as the Organisation for Economic Co-operation and Development (OECD), have published guidelines on data privacy, promoting best practices for data protection across various jurisdictions.
These initiatives highlight the shared responsibility for data privacy and security on a global scale.
Potential Collaborations Between Countries
Several potential collaborations between countries are emerging to regulate data. These include bilateral agreements on data transfer, facilitating the exchange of information and individuals’ data while upholding privacy standards. Multilateral agreements could establish regional data privacy frameworks, enabling more seamless data flows within a defined geographical area. Joint initiatives involving data protection authorities from different countries could share best practices and knowledge to enhance the efficacy of data privacy regulations.
These collaborations could result in the development of common standards and best practices for data protection.
Challenges in Achieving Global Consensus
Achieving global consensus on data privacy standards remains challenging. Different legal traditions, cultural values, and economic priorities contribute to the diversity of approaches to data privacy. Furthermore, conflicting interests between data protection and other objectives, such as economic development or national security, can complicate consensus-building efforts. Data localization policies in some countries can also create barriers to the free flow of data, leading to a fragmentation of data privacy standards.
Impact on Data Flows Between Countries
Data flows between countries are likely to be significantly impacted by international harmonization efforts. Clearer and more consistent regulations across jurisdictions will likely reduce the complexities associated with cross-border data transfers. Businesses will benefit from a more predictable regulatory environment, fostering investment and innovation. However, concerns about data security and the protection of individual rights will remain paramount, demanding robust enforcement mechanisms.
The impact of differing approaches to data privacy on international data flows will be a critical factor in the development of a global data privacy framework.
Different Approaches to International Data Privacy
| Approach | Description | Example |
|---|---|---|
| Mutual Recognition | Countries recognize each other’s data privacy standards as equivalent. | EU-US Privacy Shield |
| Model Laws | Countries adopt similar legal frameworks based on a model law. | OECD Guidelines |
| Bilateral Agreements | Agreements between two countries concerning data transfer. | Canada-EU Data Privacy Agreement |
| Regional Frameworks | Data privacy rules established for a group of countries. | The Asia-Pacific Economic Cooperation (APEC) data privacy framework |
Different approaches to international data privacy reflect the varied contexts and priorities of different countries. The table above illustrates the diverse methods employed to harmonize data privacy regulations, reflecting the complexities of achieving a unified global approach.
Data Security and Breach Notification
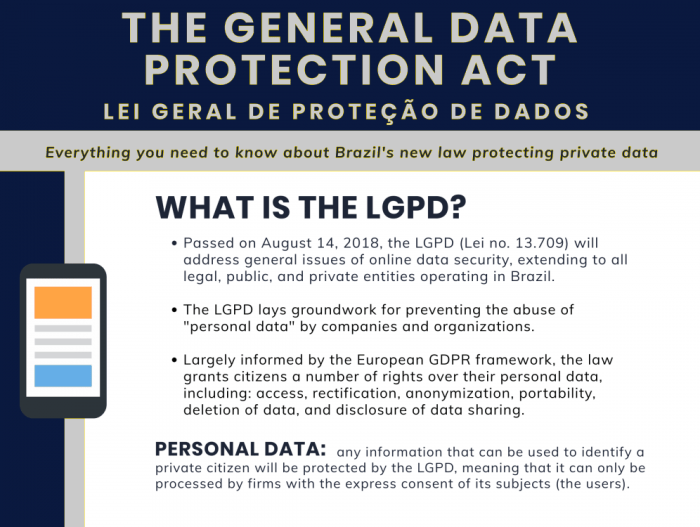
Data security is paramount in the new 2025 data privacy laws. Organizations must implement robust measures to protect sensitive personal data from unauthorized access, use, disclosure, alteration, or destruction. Effective breach notification procedures are equally crucial to mitigate the impact on affected individuals and maintain public trust. Failure to adhere to these standards can result in severe penalties.
Security Measures Expected
Organizations must implement a multi-layered approach to data security. This encompasses various technical, physical, and administrative controls. Strong passwords, encryption of data both in transit and at rest, and regular security audits are examples of crucial technical controls. Physical security measures include secure data centers and access restrictions. Administrative controls involve policies, training programs, and incident response plans.
These measures are designed to protect data from unauthorized access and misuse.
Robust Security Protocols
Implementing robust security protocols is critical for maintaining data integrity. These protocols should include:
- Regular security assessments and vulnerability scanning: Regular audits and penetration testing help identify and address security weaknesses before they can be exploited. This proactive approach minimizes the risk of breaches.
- Strong access controls: Implementing multi-factor authentication, least privilege access, and role-based access control limits access to sensitive data only to authorized personnel.
- Data encryption: Encrypting data both in transit and at rest protects data confidentiality even if unauthorized access occurs. Data encryption prevents unauthorized access and use, regardless of the method used to compromise the data.
- Regular employee training: Educating employees about data security best practices and potential threats helps prevent unintentional breaches. This training emphasizes recognizing and reporting suspicious activities.
Breach Notification Handling
Prompt and transparent breach notification is crucial. Organizations must notify affected individuals and relevant authorities within a specific timeframe. Notification procedures must adhere to established legal requirements, clearly explaining the nature of the breach, affected data categories, and steps taken to mitigate further harm.
Penalties for Data Breaches
Penalties for data breaches can be significant, varying based on the severity of the breach and the jurisdiction. These penalties can include substantial fines, legal action, reputational damage, and even criminal prosecution in severe cases. The potential penalties are substantial enough to act as a deterrent. For example, in certain jurisdictions, a large-scale data breach can result in millions of dollars in fines and substantial legal costs.
Reporting Procedures for Data Breaches
| Category | Reporting Authority | Timeframe |
|---|---|---|
| Internal | Security team/Compliance Officer | Within 24-48 hours of detection |
| External | Relevant government agencies (e.g., data protection authorities) | Within 72 hours of detection, or as mandated by law |
| Affected Individuals | Direct notification to affected individuals | Within [specific timeframe, e.g., 48 hours] |
This table Artikels a sample reporting procedure for data breaches. The specific timeframes and authorities may vary based on the jurisdiction and the nature of the breach.
Cross-border Data Transfer
Cross-border data transfers are a critical aspect of the modern digital economy, facilitating international commerce, communication, and innovation. However, the transfer of data across borders necessitates careful consideration of differing legal frameworks and potential risks. This section Artikels the mechanisms for such transfers, highlighting potential hurdles and the implications of varying data protection standards.
Mechanisms for Cross-border Data Transfers
Data transfers across international borders are governed by a complex interplay of national laws. Mechanisms employed to facilitate these transfers often involve contractual agreements, international frameworks, and standardized processes. These mechanisms aim to ensure compliance with applicable data protection regulations in both the originating and receiving countries.
Data Transfer Agreements
Data transfer agreements, such as Standard Contractual Clauses (SCCs) adopted by the European Union, serve as legally binding documents that Artikel the obligations of data controllers and processors. These agreements establish specific safeguards for the transferred data, including data security measures and the enforcement of data subject rights.
- Example 1: A US-based e-commerce company transferring customer data to a European Union-based payment processor would use SCCs to guarantee the security and privacy of the customer data. This demonstrates the transfer of data from one jurisdiction to another under a legally binding contract.
- Example 2: A multinational corporation operating in multiple countries may utilize Binding Corporate Rules (BCRs) to establish internal data transfer policies and procedures that adhere to the data protection standards of various jurisdictions. These policies address issues such as data security and access rights, promoting transparency and accountability.
Potential Hurdles in International Data Transfer
Difficulties in cross-border data transfers stem from variations in data protection laws, regulations, and enforcement mechanisms across countries. This can create obstacles for businesses and organizations seeking to transfer data internationally. Furthermore, a lack of harmonization can impede the smooth flow of information and pose challenges for compliance.
Differing Standards Across Countries
Differences in data protection standards between countries often create significant hurdles for cross-border data transfers. A country with stricter data protection regulations may impose more stringent requirements on data transfers than a country with less stringent regulations. This disparity can create inconsistencies and complexities for businesses. For instance, the EU’s General Data Protection Regulation (GDPR) has more stringent requirements for data transfers than many other regions.
Flowchart of Cross-border Data Transfer

Note: This flowchart is a conceptual representation and may vary depending on specific circumstances.
Process Steps:
- Data Controller in Country A identifies the need for cross-border transfer.
- Data Controller assesses the recipient’s legal framework and data protection standards in Country B.
- Appropriate data transfer agreements (e.g., SCCs) are negotiated and signed between parties.
- Data is transferred securely to the recipient in Country B.
- Monitoring and compliance mechanisms are implemented to ensure ongoing adherence to data protection regulations.
Enforcement and Penalties
Data privacy laws are only effective if they are rigorously enforced. Robust enforcement mechanisms are crucial to deterring violations and ensuring compliance. The potential penalties for non-compliance act as a strong deterrent and encourage organizations to prioritize data protection. This section examines the various enforcement mechanisms, potential penalties, and the role of regulatory bodies in overseeing compliance.
Enforcement Mechanisms
Effective enforcement mechanisms are essential for upholding data privacy laws. These mechanisms ensure accountability and deter future violations. Various approaches, including administrative investigations, civil lawsuits, and criminal prosecutions, are employed depending on the severity of the violation and the specific provisions of the law.
- Administrative investigations are often the first step in the enforcement process. Regulatory bodies typically conduct these investigations to determine whether a data breach or other violation has occurred. These investigations can involve examining company records, interviewing employees, and scrutinizing data handling practices.
- Civil lawsuits can be filed by individuals or organizations whose data has been compromised or who have experienced harm due to a data privacy violation. These lawsuits seek compensation for damages, including financial losses, emotional distress, or reputational harm.
- Criminal prosecutions are reserved for serious violations that involve intentional misconduct or significant harm to individuals. These prosecutions often target individuals or entities who knowingly or recklessly violated data privacy regulations.
Potential Penalties
Penalties for data privacy violations vary depending on the nature and severity of the violation. These penalties act as a strong deterrent and help ensure that organizations prioritize data protection. Fines, injunctions, and other sanctions aim to hold violators accountable.
- Fines are a common form of penalty for data privacy violations. The amount of the fine can range from a few thousand dollars to millions, depending on the severity of the violation, the number of affected individuals, and the regulatory framework.
- Injunctions are court orders that require a company to stop a particular activity, such as collecting or processing data in a way that violates the law. These orders can be crucial in preventing further harm and ensuring compliance.
- Other sanctions, such as mandatory data security training for employees or the implementation of improved data protection measures, are also frequently used. These measures help organizations prevent future violations.
Role of Regulatory Bodies
Regulatory bodies play a critical role in overseeing compliance with data privacy laws. They ensure that organizations are handling personal data responsibly and in accordance with the law.
- Regulatory bodies are responsible for interpreting and enforcing data privacy laws. They issue guidance, conduct audits, and investigate suspected violations. They also play a role in developing and promoting best practices for data protection.
- These bodies often have the power to impose penalties for non-compliance, such as fines or injunctions. This ensures that organizations are held accountable for their actions.
Examples of Fines
Significant fines have been levied in the past for data privacy violations, highlighting the importance of compliance. These examples serve as a clear indication of the potential consequences for organizations that fail to adhere to data privacy regulations.
- In one case, a major social media platform was fined millions of dollars for failing to adequately protect user data. The fine reflected the significant impact of the violation on a large number of users.
- Another example involved a healthcare provider facing a substantial fine for failing to secure patient data, demonstrating the consequences of inadequate security measures.
Penalty Table
This table illustrates potential penalties for various data privacy violations. Note that these are illustrative examples and actual penalties may vary depending on specific circumstances.
| Violation Category | Description | Potential Penalty (Illustrative) |
|---|---|---|
| Data Breach | Unauthorized access or disclosure of personal data | $1,000,000 – $10,000,000 |
| Lack of Transparency | Failure to provide adequate information about data collection practices | $50,000 – $500,000 |
| Inadequate Security Measures | Failure to implement reasonable security measures to protect personal data | $25,000 – $250,000 |
| Non-compliance with Subject Rights | Failure to respond to data subject requests or violate their rights | $10,000 – $100,000 |
Technological Implications
The rapid advancement of technology presents both opportunities and challenges for data privacy. New technologies, particularly artificial intelligence (AI) and automation, are reshaping how data is collected, processed, and used, demanding careful consideration of their impact on individuals’ rights and responsibilities. Data privacy laws must adapt to these evolving technological landscapes to ensure continued protection.
Impact of AI and Automation on Data Handling
AI and automation technologies are transforming data handling processes, often increasing the volume and velocity of data collection. AI algorithms frequently rely on vast datasets for training and operation, necessitating careful consideration of data quality, bias, and potential misuse. Automation systems may streamline data processing, but they can also mask the complex decision-making processes, making it harder to identify and address potential biases or errors.
Examples of Technology’s Impact on Existing Data Privacy Laws
Existing data privacy laws are facing challenges in adapting to the rapid development of new technologies. Consider the use of facial recognition technology. Facial recognition systems raise concerns about the potential for misuse of personal data and the lack of transparency in how these systems operate. Cloud computing, while offering significant benefits, necessitates careful consideration of data security and cross-border data transfers.
Data privacy laws in 2025 are evolving rapidly, and new technologies like Natural language processing are significantly impacting how we approach these regulations. This increased processing of vast amounts of personal data necessitates a careful balance between innovation and data protection. The challenge lies in ensuring that these new tools don’t compromise individual privacy rights while allowing for the advancement of useful applications.
These examples highlight the need for ongoing evaluation and adjustment of existing frameworks.
Challenges in Ensuring Data Privacy in New Technological Contexts
Ensuring data privacy in the face of emerging technologies presents significant hurdles. Data minimization principles become increasingly complex with sophisticated data analysis techniques. Ensuring data accuracy and preventing bias in AI algorithms is a critical challenge, as biased data can perpetuate discrimination. Maintaining user control over their data in automated systems, especially when dealing with vast datasets, requires careful design and implementation.
The use of complex algorithms can create “black boxes” where it’s difficult to understand how decisions are made, posing difficulties in accountability and oversight.
Ethical Considerations Related to Data Usage in AI Systems
Ethical considerations are paramount when using data in AI systems. The potential for AI systems to perpetuate or amplify existing societal biases requires ongoing monitoring and mitigation strategies. The development and deployment of AI systems should prioritize fairness, transparency, and accountability. These considerations are essential to prevent discrimination and promote equitable outcomes. Data subjects must be provided with clear and accessible information about how their data is being used in AI systems.
This includes details about the data collected, the purpose of the analysis, and the potential consequences of the results. Ensuring the ethical use of data is essential for building trust and preventing harm.
Impact on Businesses and Consumers
The 2025 data privacy laws represent a significant shift in how businesses handle personal data and consumer expectations. These regulations aim to empower consumers with greater control over their information while simultaneously requiring businesses to adopt robust data protection practices. The impact on both businesses and consumers is multifaceted, ranging from operational adjustments to consumer empowerment.
Effects on Businesses
Businesses face a range of adjustments in their operations to comply with the 2025 data privacy laws. These regulations demand a fundamental shift in data management strategies, from collection practices to data retention policies. Maintaining compliance necessitates careful consideration of data security protocols, transparency in data handling, and the implementation of robust mechanisms for data subject rights requests.
- Enhanced Security Measures: Businesses must implement advanced security measures to protect sensitive consumer data from unauthorized access, breaches, and misuse. This includes robust encryption, access controls, and regular security audits.
- Data Minimization and Purpose Limitation: Businesses must collect only the data necessary for the specified purpose and limit its use to those pre-defined purposes. This necessitates a re-evaluation of existing data collection practices.
- Transparency and Consent: Clear and concise communication with consumers regarding data collection practices is essential. Businesses must obtain explicit consent for data processing and provide comprehensive information about how data will be used.
- Data Subject Rights Management: Businesses need to establish efficient processes for handling data subject requests (e.g., access, rectification, erasure, and restriction of processing). This includes dedicated teams and clear procedures for responding to these requests promptly.
Consumer Data Protection
These laws fundamentally alter the landscape of consumer data protection, granting consumers greater control over their personal information. Consumers will now have more rights to access, correct, or delete their data, and businesses will need to respect these rights. The shift towards consumer empowerment underscores the importance of responsible data handling.
- Increased Consumer Control: Consumers will have greater control over how their data is collected, used, and shared. This includes the ability to request access to their data, modify inaccurate information, and potentially limit data sharing.
- Enhanced Transparency: Consumers will gain greater transparency into how businesses handle their data. This includes understanding the purposes for data collection, how it’s processed, and who has access to it.
- Protection from Misuse: Consumers will be better protected from data breaches and misuse of their personal information. Robust data protection mechanisms and enforcement will minimize potential risks.
Business Strategies for Compliance
Adopting proactive strategies is crucial for businesses to meet the 2025 data privacy regulations. Businesses should anticipate the requirements and proactively implement solutions.
- Data Mapping and Inventory: Thorough data mapping will help identify all personal data held by the business and the purpose for which it is used. This will enable businesses to streamline compliance efforts.
- Policy Review and Update: Existing data privacy policies should be reviewed and updated to reflect the new regulations. This ensures alignment with legal requirements and transparency for consumers.
- Employee Training: Employees need training on the new regulations and their responsibilities regarding data handling. This ensures consistent application of the new standards.
Potential Consumer Benefits
Enhanced data privacy laws will offer consumers significant benefits. Improved control over personal information and increased transparency are key advantages. Protection from data misuse and breaches will enhance consumer trust and confidence.
- Greater Trust in Businesses: Businesses that proactively implement data privacy practices will foster greater consumer trust and loyalty. This is achieved by demonstrating a commitment to protecting consumer data.
- Empowerment over Personal Information: Consumers will have more control over how their personal data is handled, used, and shared. This translates into greater agency in the digital sphere.
- Protection from Harm: Improved data privacy laws will safeguard consumers from potential harm arising from data breaches and misuse. This will reduce the risk of identity theft and other related issues.
Hypothetical Scenario
Imagine a retail company, “Trendy Threads,” that sells clothing online. They recognize the upcoming 2025 data privacy laws and decide to proactively adapt. They update their website to clearly Artikel their data collection practices and obtain explicit consent for data processing. They implement enhanced security measures to protect customer data, map all personal data, and train their staff on the new regulations.
This proactive approach positions Trendy Threads for compliance and enhances consumer trust.
Industry-Specific Considerations
Data privacy laws are not a one-size-fits-all solution. Different industries face unique challenges when implementing and adhering to these regulations. Understanding these nuances is crucial for effective compliance and minimizing potential risks. Tailored data protection strategies are essential for organizations to mitigate risks and ensure responsible data handling.
Healthcare Industry Implications
The healthcare sector handles highly sensitive personal data, including medical records and genetic information. Maintaining confidentiality and ensuring patient privacy is paramount. Stricter regulations are necessary to protect this sensitive data from unauthorized access and misuse. This requires robust security measures and adherence to strict protocols for data storage, access, and transfer. Data breaches in healthcare can have severe consequences, including reputational damage and financial penalties.
Best Practices in Healthcare
- Implementing strong access controls and encryption protocols for electronic health records (EHRs).
- Developing clear policies and procedures for handling patient data requests, including access, correction, and deletion requests.
- Regularly assessing and updating security measures to address evolving threats and vulnerabilities.
- Providing comprehensive training to employees on data privacy regulations and best practices.
Financial Industry Implications
The financial sector deals with a vast amount of sensitive financial data, including account information, transaction details, and customer identification numbers. Protecting this data from theft and misuse is critical to maintaining trust and avoiding significant financial losses. Regulations for financial institutions are often more stringent to address the inherent risks associated with this sector. Data breaches in finance can lead to identity theft, fraud, and significant reputational damage.
Best Practices in Finance
- Implementing multi-factor authentication (MFA) for all user accounts to enhance security.
- Regularly reviewing and updating security protocols to align with the latest industry standards.
- Employing secure data storage solutions, including encryption and access controls.
- Educating staff on data security best practices and compliance procedures.
Importance of Tailored Strategies, Data privacy laws 2025
Developing a comprehensive data protection strategy that aligns with the specific needs and requirements of the industry is critical for organizations. A one-size-fits-all approach often fails to address the unique challenges and risks faced by specific sectors. This requires tailored strategies for compliance, data governance, and incident response. The strategy should consider the potential risks of data breaches and other vulnerabilities.
Industry Compliance Needs
| Industry | Potential Compliance Needs |
|---|---|
| Healthcare | Stricter regulations on patient data, robust security measures, and stringent access controls. |
| Finance | Robust security protocols, encryption, and compliance with stringent financial regulations. |
| Retail | Data minimization principles, transparent data collection practices, and security protocols for customer information. |
| Technology | Data security measures, responsible use of personal data, and clear data governance policies. |
| Education | Student data privacy, data minimization, and secure storage and access protocols. |
Emerging Trends and Future Predictions
The landscape of data privacy is constantly evolving, driven by technological advancements, societal concerns, and international collaborations. Understanding these trends is crucial for businesses and individuals to adapt and navigate the future of data protection effectively. This section explores key emerging trends and potential future developments in data privacy.
Data privacy laws in 2025 are set to be significantly impactful, especially considering their application to emerging technologies like Machine learning applications. These laws will need to carefully balance the potential benefits of these advancements with the need to protect individual data. The evolving landscape of data usage necessitates a robust and adaptable approach to data privacy legislation.
Emerging Trends in Data Privacy
Several trends are reshaping data privacy regulations and practices. These include the increasing use of artificial intelligence (AI) and machine learning (ML) in data processing, the growing importance of data minimization principles, and the development of innovative data security technologies. A key driver is the growing awareness of the ethical implications of data use.
- AI and Machine Learning: The integration of AI and ML in data processing necessitates careful consideration of data privacy implications. Bias in algorithms, the potential for unintended discrimination, and the need for explainable AI are crucial areas of concern. For instance, facial recognition technology raises questions about surveillance and potential misuse of data.
- Data Minimization: Data minimization principles are becoming more widely adopted. Regulations are increasingly emphasizing the collection of only necessary data and the minimization of data retention periods. This approach aligns with the ethical imperative to respect individual privacy.
- Data Security Technologies: The development of robust and adaptable data security technologies, such as encryption and secure data storage solutions, remains paramount. The evolution of these technologies, along with the increasing sophistication of cyberattacks, necessitates continuous vigilance and investment in cutting-edge security measures.
- Ethical Considerations: Growing awareness of the ethical implications of data use is driving a shift towards more responsible data practices. This includes a focus on transparency, accountability, and fairness in data collection and processing. Companies are increasingly recognizing the need to address ethical concerns surrounding data usage, such as bias in algorithms and potential misuse of personal information.
Potential Future Developments in Data Privacy
Anticipating future developments in data privacy requires careful analysis of evolving technologies and societal needs.
- Data Sovereignty and Localization: Data sovereignty, or the right of a nation to control data collected within its borders, is gaining traction. Countries may impose stricter regulations on cross-border data transfers, potentially leading to a fragmentation of data privacy laws.
- Decentralized Data Management: Blockchain technology and other decentralized data management systems may offer alternative approaches to data storage and processing. These systems can enhance data security and individual control over personal information, while potentially challenging traditional centralized data structures.
- Data Privacy by Design: The principle of data privacy by design emphasizes integrating data protection considerations into every stage of product development and service design. This preventative approach aims to minimize the risks associated with data collection and use.
- Increased Consumer Awareness: Consumers are increasingly aware of their data rights and actively seeking greater control over their personal information. This heightened awareness will likely influence business practices and drive the demand for more robust data privacy protections.
International Cooperation in Shaping the Future of Data Privacy
International cooperation is essential for harmonizing data privacy standards across borders. Mutual recognition of data protection principles and enforcement mechanisms will be critical in the digital age.
- Harmonization of Regulations: Efforts to harmonize data privacy regulations across different jurisdictions will be crucial for fostering a global ecosystem that respects individual privacy while facilitating cross-border trade and innovation.
- International Data Privacy Forums: Continued dialogue and cooperation through international data privacy forums can lead to the development of shared best practices and guidelines for data protection.
- Cross-border Data Transfers: Establishing clear guidelines for cross-border data transfers will be critical to ensuring the free flow of data while upholding data privacy rights.
Importance of Staying Informed About Evolving Landscape
The data privacy landscape is dynamic and complex, demanding ongoing vigilance and adaptability.
- Continuous Monitoring: Staying informed about the evolving landscape of data privacy is essential for individuals and organizations to adapt to changes in regulations and best practices.
- Adapting to Changes: Businesses must be prepared to adapt their practices to the evolving legal and technological requirements of data privacy.
Potential Future Challenges in Data Privacy
The future of data privacy presents a range of challenges, particularly concerning the balance between data use and individual rights.
- Balancing Innovation and Privacy: Balancing the potential benefits of data-driven innovation with the need to protect individual privacy will remain a key challenge.
- Enforcement Gaps: Effective enforcement of data privacy regulations is critical, but enforcement gaps may hinder the protection of data rights.
- Data Breaches and Cybersecurity: Data breaches and cybersecurity threats remain significant concerns. The need for robust security measures and incident response plans is paramount.
Closing Summary
In conclusion, data privacy laws 2025 represent a substantial evolution in data governance. These laws are designed to enhance data security, empower individuals, and foster international cooperation. Businesses and individuals alike must prepare for the changes ahead to maintain compliance and thrive in this new data-centric environment. This evolution signifies a crucial step towards responsible data handling in the digital age.
Answers to Common Questions
What are the key principles behind the anticipated data privacy laws of 2025?
The core principles likely include enhanced data subject rights, robust data security measures, and international harmonization of regulations. Specific principles will vary by jurisdiction but will likely prioritize individual control over their data, data minimization, and purpose limitation.
How will data breaches be handled under the 2025 laws?
Notification procedures and penalties for data breaches will likely be more stringent than existing regulations. The precise procedures, timelines, and severity of penalties will depend on the specific jurisdiction and the nature of the breach.
What are some examples of how the 2025 laws might differ from existing regulations?
Potential differences include broader data subject rights, stricter cross-border transfer requirements, and more comprehensive breach notification procedures. Specific differences will depend on the specific laws enacted in each jurisdiction.
What are the potential penalties for violating data privacy laws in 2025?
Penalties for violations will likely include significant fines, injunctions, and other legal remedies. The severity of penalties will likely depend on the nature and scope of the violation.






